12.16.198.1100: System Traffic Analysis
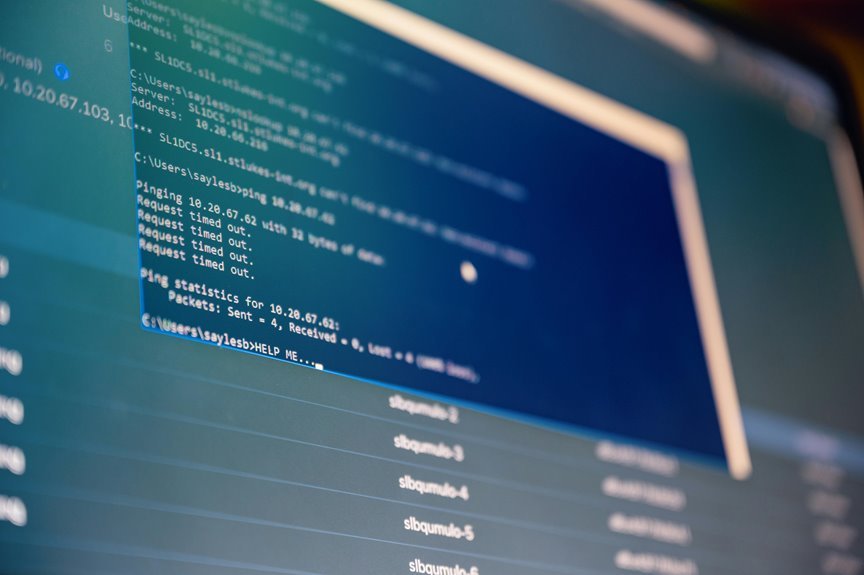
The IP address 12.16.198.1100 serves as a case study in the realm of system traffic analysis. It highlights the necessity for advanced methodologies such as packet inspection and statistical analysis. These techniques provide network administrators with critical insights into traffic behavior and potential vulnerabilities. As the landscape of network operations becomes more intricate, the integration of real-time analysis and AI promises to transform these practices. What challenges and innovations lie ahead in this evolving field?
Historical Context of Traffic Analysis
Although traffic analysis has evolved significantly over the decades, its roots can be traced back to early methods of data collection and observation in the field of telecommunications.
The historical significance of these early techniques lies in their foundational role, enabling the systematic examination of communication patterns.
Such initial approaches paved the way for modern analytics, emphasizing the importance of data in enhancing operational efficiency and user autonomy.
Methodologies for Analyzing System Traffic
A variety of methodologies exist for analyzing system traffic, each tailored to address specific analytical needs and contexts.
Packet inspection techniques allow for deep examination of data packets, revealing underlying traffic patterns.
Statistical analysis further identifies anomalies and trends, providing insights into network behavior.
These methodologies empower network administrators to optimize performance and enhance security, ultimately contributing to a more resilient and efficient system environment.
Implications for Modern Network Operations
As organizations increasingly rely on complex network infrastructures, the implications of traffic analysis for modern network operations become paramount.
Effective traffic analysis enhances network security by identifying vulnerabilities and mitigating threats.
Furthermore, it plays a crucial role in safeguarding data privacy, ensuring compliance with regulations.
Conclusion
In the intricate tapestry of modern network operations, system traffic analysis emerges as a vital thread, weaving together efficiency and security. By harnessing methodologies like packet inspection and statistical analysis, network administrators illuminate hidden patterns and vulnerabilities, much like a lighthouse guiding ships through treacherous waters. As the digital landscape continues to evolve, the integration of real-time analysis and AI stands poised to transform these practices, fortifying the very foundations of data privacy and operational integrity in an increasingly complex world.